
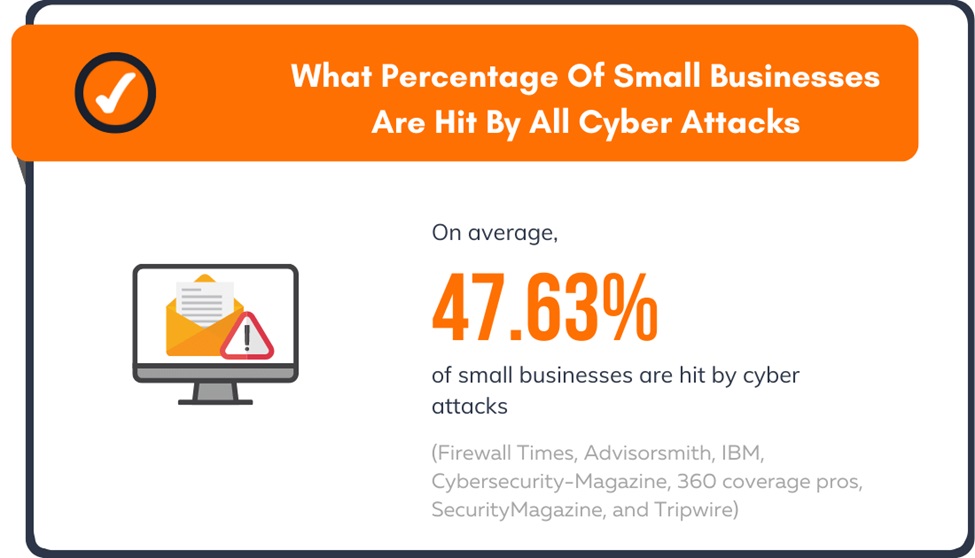
When it comes to launching cyber attacks, small businesses are an attractive prey in the eyes of hackers. In fact, according to strongdm, 46% of all cyber breaches come from businesses with fewer than 1,000 employees. Many small businesses make the mistake of believing that their operations are far too small to be seen as valuable targets of an attack.
However, hackers acknowledge this thinking to subject their most popular attacks, like phishing campaigns against unsuspecting employees. Due to their weaker security measures and the fact that many small businesses might not be financially prepared for a cyber attack, mainly due to their lack of cyber insurance and financial security, many hackers find themselves more successful in planning their malicious endeavors against small businesses than large ones. For small businesses, the effects of even one cyber breach can be devastating and powerful enough to put them entirely out of business.
The Importance of Implementing Effective Cyber Security Measures
One of the most effective ways to protect against cyber attacks is by preventing them in the first place. This means enabling the right authentication and authorization practices and other measures to protect the confidentiality, integrity, and access to customer and system data.
As we head into 2024, implementing securing measures in IT systems will become even more crucial for businesses. That’s why, in this article, we will discuss the top 15 cyber security best practices that every business will want to implement into their organization within the coming year.
1. Password Management System
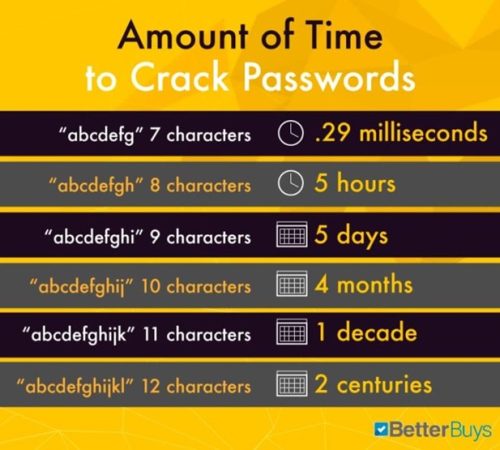
As businesses continue to grow, they can expect to bring in more and more employees and customers with accounts that handle sensitive data that need to be protected. That’s why, in 2024, it will be more important than ever for companies to implement password management systems into their business practice. This includes password strength meters, password encryption systems, password managers, and support for two-factor authentication.
2. Educate Workers and Customers About Zero Trust
According to the US. Office Of Management and Budget, the US Federal government is moving toward a zero-trust architecture strategy by the end of 2024 to prevent cyber security breaches and upscale the government’s defenses against more advanced threat campaigns. Implementing a zero-trust architecture means that no person or technology should automatically be deemed trustworthy before being allowed access to any network.
Users and their devices should go through thorough authentication and authorization methods to ensure they have the proper verifications before trying to access a resource or system. Zero Trust can save organizations up to $1 million in data breach costs compared to businesses that don’t use zero trust systems.
3. Enable Next-Generation Cyber Security Technology
Gone are the days when businesses and their workers can solely rely on firewalls and IDS technology to prevent cyber attacks and protect their systems. As we head into the future, businesses can expect to use more next-generation cybersecurity technologies in the form of AI and machine learning to automate the detection of threats. Companies can also benefit from incorporating blockchain technology into their security toolboxes. This technology can work to create a secure and tamper-proof record of data transactions and protect sensitive data.
4. Enhancing IOT Security
By 2024, the number of IOT devices connected to the internet is expected to reach 83 billion. Though IoT devices have undoubtedly increased in popularity over the years, many are unaware of the vulnerabilities that continue to lie within these systems. 32% of companies that have adopted IoT devices are experiencing data security issues because of their lack of skilled personnel. Some of the most important security practices that IOT device operators will need to consider for 2024 can be seen below:
- Change default passwords.
- Keep software patches up to date.
- Encrypt the data that IoT devices are sending and receiving.
- Disable unnecessary features.
- Implement multi-factor authentication.
5. Patch Management and Misconfiguration Management
Each year, network systems and software versions head closer to reaching the end of their lives. End of life means that the software will no longer be supported with updates by its vendor, leaving it more vulnerable to cyber attacks over time.
That’s why, as we head into 2024, it’s crucial to implement a thorough patch management system that may include updating your operating system, web browser, email clients, and firmware to the latest versions. Companies should also implement a system development life cycle process where sensitive data within old operating systems are discarded properly.
6. Comply With Privacy Laws and Data Regulations
By the end of 2024, nearly 75% of the world’s population will have its data covered under modern privacy regulations. In 2024, we can expect to see organizations combine advanced technologies like AI and machine learning to enhance data security.
One example is privacy-preserving machine learning (PPML), where Machine Learning can train itself on data without decrypting and exposing sensitive information such as medical records or credit card numbers.
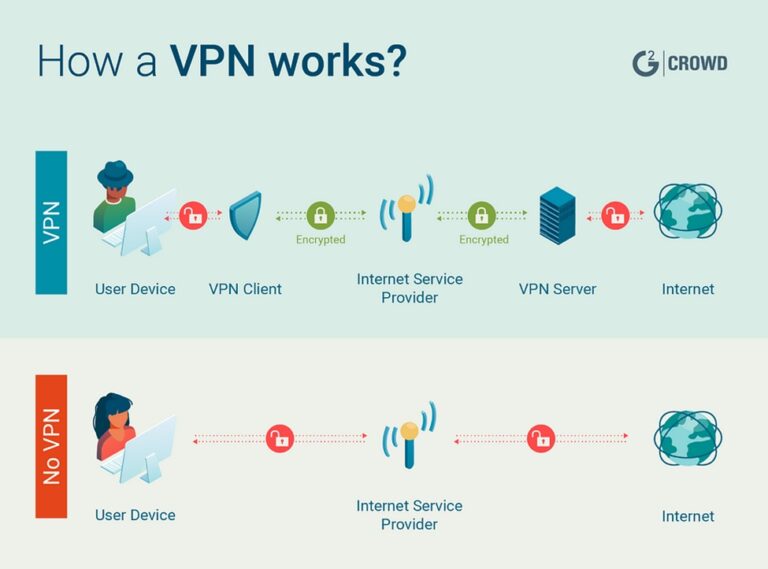
7. Enable Secure Remote Working Environments With a VPN
There are an increasing number of workers who have officially ditched their cubicle as their prime location to get work done. Whether choosing to work from the local coffee shop or simply from their home office, many workers use a virtual private network as a secure gateway to connect to their office’s network from nearly any remote location.
Many VPNs, like Proton VPN, are free applications that users can download. When using a VPN, all your internet traffic is encrypted, and your IP address is hidden from potential attackers.
8. Human-Centric Design
According to Verizon, nearly 82% of data breaches are caused by human error. Some of the most common human errors come from employees falling for phishing scams or simply using an easy-to-guess password.
This makes it easy to see how nearly 42% of workers have admitted to making a dangerous action online that threatens the digital security of their organization. To prevent social engineering attacks, it’s important to understand the psychology of both employees and hackers.
Employees should be notified of the latest phishing and social engineering campaigns that are impacting organizations around them. They should be encouraged not to open emails or engage with any text messages or phone calls that they may find suspicious.
Workers should consider keeping privacy screens that hide information on their desktops as people walk by them. This measure can further protect sensitive and confidential data against insider threats.

9. Protection Against Automotive Hacking
Undoubtedly, the automotive industry continues to experience a digital transformation in the type of services and features that new cars can provide -whether it be their built-in dashcam, music-streaming services, GPS systems, or more.
Unfortunately, this also means that the automotive industry is bound to experience more cyber-attacks as 2024 approaches.
Automotive cyber-attacks have increased by 225% from 2018 to 2021. That’s why organizations based in the automotive industry and the everyday user that owns a smart car should consider implementing the following cyber security best practices when securing their vehicle.
- To prevent GPS hacking using a radio system, users should only enable and control access to their GPS when needed.
- Users should change the default passwords that come with their car’s built-in systems. Also, authorized users should pair secure and strong passwords used with their vehicle’s systems with MFA and/or biometric authentication.
10. Enabling Secure Software Development and Coding
According to VentureBeat, the annual revenue for security-based software was estimated to be worth nearly $61.38 billion in 2021. One of the main practices organizations can implement to make their applications safer is enforcing API access controls.
APIs are a set of rules that allow different applications to communicate with each other. If an API is enabled with weak access controls, it can lead to unauthorized access to private user and IT system information.
Given how nearly 57% of web applications use APIs as of 2023, security professionals should consider the following practices to secure their APIs for 2024.
- Ensure all the data transported by APIs and web browsers is secured by TLS encryption.
- Always validate and analyze the input of data that an API creates before the data is transported to an endpoint.
- Limit the number of requests that are being made to an API. Some requests may be part of an automated attack.
11. Enabling Elastic Log Monitoring for Big Data Sets
These days, security professionals are monitoring and collecting information from more systems than ever. Within 2024, we are bound to see organizations upgrade their traditional log systems to elastic log monitoring systems.
Unlike traditional systems, elastic log systems are more scalable and flexible and can handle large volumes of data from different applications, compute, network, and storage systems.
Additionally, elastic log monitoring systems are a step up from traditional systems since elastic logs can provide real-time insights into the behavior and performance of network devices.
12. Quantum-Resistant Encryption Algorithms
As we head into 2024, hackers seek more advanced ways to break the encryption algorithms that make up our secure passwords. Using the power of quantum mechanics, supercomputers can perform calculations at a rate much quicker than regular computers.
This makes quantum computers a potential tool hackers can use for engaging in data breaches and ransomware attacks.
The National Institute of Standards and Technology (NIST) has been developing quantum-resistant encryption algorithms since July 2022 to combat this growing threat. By 2024, these algorithms are expected to become part of NIST’s post-quantum cryptographic standard.
These standards will be what organizations will want to abide by and implement into their security operations.
13. Consider Cyber Insurance
As companies continuously find themselves protecting against and being aware of the prominence of cyber threats, more and more businesses are finding themselves up in arms against the potential of data breaches.
That’s why many businesses in 2024 will be reaching out to protect their assets with cyber insurance. This form of insurance can help businesses pay any legal fees, regulatory fines, public relations expenses, and any loss of revenue due to a data breach. According to Insureon, small businesses can find themselves paying up to $145 a month on cyber insurance.

14. Consider Cloud Data Backup
Businesses are always looking for ways to cut costs on their daily operations and the security systems they use. Companies can achieve this objective using cloud-based data backups instead of onsite physical data servers.
84% of businesses as far back as 2019 used cloud systems for data storage. According to Forbes, businesses have saved between 30-50% a year by transporting their data to the cloud.
15. Implementing More Secure SSO Authentication Practices
An increasing number of businesses have improved their users’ convenience and ease of using their applications through SSO authentication. Single sign-on allows a user to log into multiple applications, whether Facebook, LinkedIn, or another website using the same credentials.
Though SSO makes signing into important systems like bank accounts a fast process, the authentication method comes with some unfortunate risks. If a user has an insecure login credential in the form of a weak password, their identity could easily be confiscated. Attackers will then be able to access all their accounts that are associated with their weak SSO credentials.
That’s why, in 2024, we are bound to see security professionals implement multi-factor authentication (MFA) alongside SSO and use password management systems and security audits to ensure that SSO is safe for users.
Conclusion
Whether using AI to upgrade the confidentiality of data or implementing a robust password management system to protect against SSO attacks, every business should be vigilant when preventing cybersecurity risks. By considering these top 15 cyber security practices, organizations can strive to stay safe from attacks in 2024.
Frequently Asked Questions "FAQs"
Q1 How much does it cost to implement these cybersecurity practices in a business?
According to Investguiding, organizations may end up using 10% of their dedicated IT budget on their cybersecurity strategy and operations.
Q2 Should even small businesses invest in vulnerability assessment and penetration tests?
It’s reasonable for small businesses to be hesitant when deciding whether to implement penetration tests and assessments into their security measures. A small-scale test can range from $3000 to a staggering $10,000 per test.
However, many would consider the price of these tests to be worth it, given how nearly 73% of successful data breaches on businesses were done by penetration testing a business’s weak web application.
Ultimately, the decision to implement a security test is made by the IT professionals of an organization based on the goals and objectives of their business.

