Why you require your email domain to be complaint to SPF, DKIM and DMARC?
Email service has been now most essential service for any business to function. It also become one of the effective, legitimate and necessary means of communication for every individual
So, looking at this it become very vital to secure this service. SPF, DKIM and DMARC are the most prominent steps towards the Email security.
It helps to ensure that the email received from your email domain has come from your legitimate source. It basically helps to protect your email domain from being used for Spoofing and sending phishing email by any malicious source.
In this article we will go into first basic understanding of SPF, How it works and also touch base on how we can configure it in Office 365
What is SPF?
Understanding SPF in detail
To understand the SPF better let us first understand some basics of email format. As part of that let us understand what are the different section of email
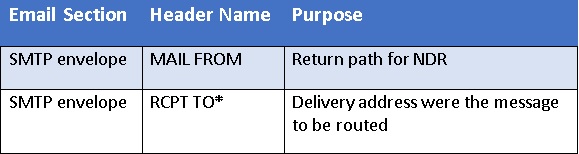
There are two important sections of any email
1. Envelop
The envelope is used by the email servers for routing email, envelope contains the address where the message must be delivered i.e. Recipient email address, and the return address of the sender called Mail From” address.
Just consider the postal letter we send. The letter is sent inside the envelop. The envelop contains sender address and the recipient address. The post office which delivers the envelop do not know what is there in letter inside the envelop. The letter head inside may refer to some other
person as sender then it actually mentions in Sender address in envelop
“Mail From” address in the envelop technically referred to as 5321 from address (RFC.5321) It specifies where to send return notices if any problems occur with the delivery of the message, such as non-delivery notices. It is not usually displayed by your email application.
2. Message
Message consist of two sub section Message header and Message body
Message Header:
Email header provides a list of technical details about the message, such as the sender address, the recipient, the time and the subject of the email etc. below are the key information there in header
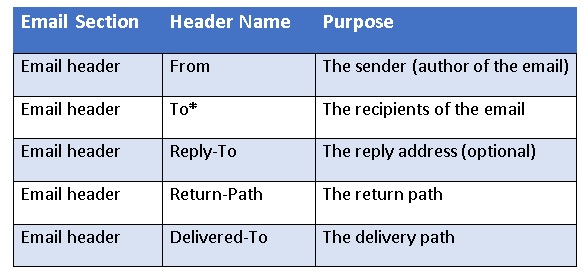
The address displayed as the From address in email header identifies the author of the email. That is, the mailbox of the person or system responsible for writing the message. Email address mentioned in this is displayed by your email client as Sender of the email. When the recipient reply back to the email it is sent to email mentioned in the From address. Its technically referred to as 5322 From address (RFC. 5322).
Message body:
It contains actual content of the message. It consists of plain text, or styled content in HTML and it may also contain file attachments.
As you see when you send the email there are two places From email address is written one in message Envelop “Mail From” address and other in Message Header “From” address. We have also understood the purpose of both
SPF record only specify the legitimate source for the email domain of email address mentioned in the Mail From address.
How does SPF work?
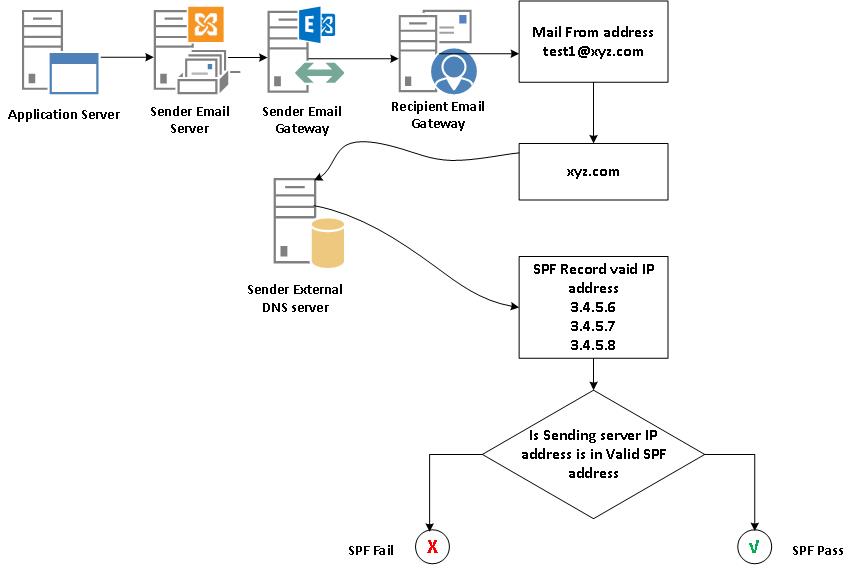
Below diagrams explains how the SPF works
Step 1 : Application send the email to Smart host that is Sender Email server, to relay it to recipient testrec@abc.com. From email address is kept as test1@xyzaccountteam.com and Mail From address is kept as test1@xyz.com
Step 2 : Sender email server send the email to Sender email gateway server. Message hygiene is done at Sender email server and then delivered to the Recipient Email gateway server over Internet.
Step 3 : Recipient Email Gateway server queries the Sender external DNS server whether SPF record been created for the Email domain mentioned in the Mail From Address. If yes what are the valid sender public IP been given in the record.
Step 4 : Once received valid sender public IP it verifies whether the public IP of the Sender of this email is mentioned in it. If yes it will mark as SPF pass and do the further processing of the email. If no it mark it as SPF fail and rejects the email.
SPF Limitation
As SPF only validate email domain mentioned in the Mail From address and not From address. This can be exploited by the spoofer to send the spoofing email using your email domain as given below
Suppose your company name is xyz.com and spoofer email domain is abc.com.
Then he or she will send the email with From Email ID having email domain xyz.com and Mail From email ID having email domain abc.com.
Spoofer will publish the SPF record for abc.com. When the recipient email gateway server receives the email, it validates sender public IP is mentioned in the SPF record of email domain abc.com and it accepts the email. Since xyz.com email domain which is mentioned in From Email address has only SPF record and No DMARC it will not be validated. (I will explain DMARC in detail in my next article)
When the recipient receives the email, it will see it as if it has come from xyz.com which is of your company and consider the email as genuine.
Understand the SPF record
SPF records are typically defined using the TXT record type. There’s also an SPF record type, but it’s deprecated, and you should always have at least the TXT record definition present, even if you use the SPF type.
SPF records are defined as a single string of text. Here’s an example record:
v=spf1 a mx ip4:69.64.153.131 include:_spf.google.com ~all
v=spf1 include:spf.protection.outlook.com -all
The SPF record starts with the v. This indicates the SPF version that is used. The current version is spf1 and it is the most common version of SPF that is understood by messaging environment.
There are many terms that can be used to define the rules based on which hosts are allowed to send mail from the domain. These terms can also be used to provide additional information for processing the SPF record. Terms are made up of mechanisms and modifiers. Below are the list of mechanisms which can be defined in SPF record
- all
- include
- a
- mx
- ip4
- ip6
- exists
The following mechanisms define which IP addresses are allowed to send mail from the domain:
all :
These term in the SPF record defines what policy should be applied when ISPs detect a server which is not listed in your SPF record.
-all : It specifies If the email is received from a server that isn’t listed are not authorized to send email and should be rejected
~all : It specifies If the email is received from a server that isn’t listed, should be accepted but tagged as a soft fail, the receiving ISP can use that as an additional factor in scoring the message’s likeliness of being spam
+all : It specifies that any server can send email from your domain (It is strongly recommended not to use this option)
a : An A record of the queried email domain or explicitly specified domain contains the IP address of the valid sender
Example
“v=spf1 a ~all”
In this example a record of queried email domain contains the IP address of the valid sender
“v=spf1 a:xyz.com ~all”
In this example a record of the domain xyz.com contains the IP address of the valid sender
“v=spf1 a/24 a:xyz.com/24 ~all”
In this example If xyz.com resolves to 1.1.1.1, the ips of entire subnet 1.1.1.0/24 would be valid sender
mx :
An MX record of the queried email domain or explicitly specified domain contains the IP address of the valid sender
Example
“v=spf1 mx ~all”
In this example mx record of queried email domain contains the IP address of the valid sender
“v=spf1 mx:xyz.com ~all”
In this example mx record of the domain xyz.com contains the IP address of the valid sender
ip4 :
Example It specifies IP address of the valid sender or the IPv4 subnet whose IPs are all valid sender
“v=spf1 ip4:192.168.0.1/16 ~all”
In this example any IP address between 192.168.0.1 and 192.168.255.255 are allowed sender
ip6 :
It specifies IP address of the valid sender or the IPv6 subnet whose IPs are all valid sender
Example
“v=spf1 ip6:2a05:c018:e3:7c00:bb71:dea8:8c53:751e ~all”
In this example specified IPv6 address 2a05:c018:e3:7c00:bb71:dea8:8c53:751e. is valid sender
Include :
It specifies the domain specified in the include statement contains the IP address of the Valid sender. If the lookup does not return a match or an error, processing proceeds to the next directive in the SPF record.
Example
“v=spf1 include:xyz.com ~all”
In this example ip addresses allowed in the spf record of xyz.com domain will be valid sender
SPF modifiers
Modifiers are name/value pairs (separated by an = sign) that provide additional information. Modifiers should appear at the end of the SPF record. A modifier may not appear more than once and unrecognized modifiers are ignored.
Redirect :
The redirect modifier is only used if no other mechanism matches.. Unlike an include mechanism, once a redirect has been navigated it will not return to evaluate further terms, for clarity it should appear as the last term in the record since it will only be evaluated if none of the mechanisms match the email sender, however its position in the SPF record will not determine its order of processing.
You cannot use redirect in combination with all, because the all mechanism will always match, and so the redirect will never be processed.
Example
“v=spf1 mx include:spf.protection.outlook.com redirect=abc.com”
In this example if the sender ip address is not in the allowed ip address of SPF record of spf.protection.outlook.com, then it will check the allow ip addresses in the SPF record of abc.com. This will be the final check and it will not evaluate further any mechanism.

